- Man Openssh Sftp-server
- Man Opens Sharks Mouth
- Man Openssh
- Man Openssh-server
- Openssh Man Ssh-keygen
- Openssh Client Windows 10
Normal OpenSSH development produces a very small, secure, and easy to maintain version for the OpenBSD project. The OpenSSH Portability Team takes that pure version and adds portability code so that OpenSSH can run on many other operating systems (Unfortunately, in particular since OpenSSH does authentication, it runs into a.lot. of differences between Unix operating systems).
- From man ssh: /.ssh/identity /.ssh/iddsa /.ssh/idrsa Contains the private key for authentication. These files contain sensitive data and should be readable by the user but not acces- sible by others (read/write/execute). Ssh will simply ignore a private key file if it is accessible by others.
- OpenSSH is a derivative of the original and free ssh 1.2.12 release by Tatu Ylonen. Aaron Campbell, Bob Beck, Markus Friedl, Niels Provos, Theo de Raadt and Dug Song removed many bugs, re-added newer features and created OpenSSH. Markus Friedl contributed the support for SSH protocol versions 1.5 and 2.0.
scp — OpenSSH secure file copy
scp | [-346ABCpqrTv] [-ccipher] [-Fssh_config] [-iidentity_file] [-Jdestination] [-llimit] [-ossh_option] [-Pport] [-Sprogram] source ... target |
scp copies files between hosts on a network.
It uses ssh(1) for data transfer, and uses the same authentication and provides the same security as a login session. The scp protocol requires execution of the remote user's shell to perform glob(3) pattern matching.
scp will ask for passwords or passphrases if they are needed for authentication.
The source and target may be specified as a local pathname, a remote host with optional path in the form [user@]host:[path], or a URI in the form scp://[user@]host[:port][/path]. Local file names can be made explicit using absolute or relative pathnames to avoid scp treating file names containing ‘:’ as host specifiers.
When copying between two remote hosts, if the URI format is used, a port may only be specified on the target if the -3 option is used.
The options are as follows:
-3scp cannot ask for passwords or passphrases for both hosts.-4scp to use IPv4 addresses only.-6scp to use IPv6 addresses only.-A-B-C-C flag to ssh(1) to enable compression.-ccipher-Fssh_configssh. This option is directly passed to ssh(1).-iidentity_file-Jdestinationscp connection to the jump host described by destination and then establishing a TCP forwarding to the ultimate destination from there. Multiple jump hops may be specified separated by comma characters. This is a shortcut to specify a ProxyJump configuration directive. This option is directly passed to ssh(1).-llimit-ossh_optionssh in the format used in ssh_config(5). This is useful for specifying options for which there is no separate scp command-line flag. For full details of the options listed below, and their possible values, see ssh_config(5). - AddressFamily
- BatchMode
- BindAddress
- BindInterface
- CanonicalDomains
- CanonicalizeFallbackLocal
- CanonicalizeHostname
- CanonicalizeMaxDots
- CanonicalizePermittedCNAMEs
- CASignatureAlgorithms
- CertificateFile
- ChallengeResponseAuthentication
- CheckHostIP
- Ciphers
- Compression
- ConnectionAttempts
- ConnectTimeout
- ControlMaster
- ControlPath
- ControlPersist
- GlobalKnownHostsFile
- GSSAPIAuthentication
- GSSAPIDelegateCredentials
- HashKnownHosts
- Host
- HostbasedAcceptedAlgorithms
- HostbasedAuthentication
- HostKeyAlgorithms
- HostKeyAlias
- Hostname
- IdentitiesOnly
- IdentityAgent
- IdentityFile
- IPQoS
- KbdInteractiveAuthentication
- KbdInteractiveDevices
- KexAlgorithms
- KnownHostsCommand
- LogLevel
- MACs
- NoHostAuthenticationForLocalhost
- NumberOfPasswordPrompts
- PasswordAuthentication
- PKCS11Provider
- Port
- PreferredAuthentications
- ProxyCommand
- ProxyJump
- PubkeyAcceptedAlgorithms
- PubkeyAuthentication
- RekeyLimit
- SendEnv
- ServerAliveInterval
- ServerAliveCountMax
- SetEnv
- StrictHostKeyChecking
- TCPKeepAlive
- UpdateHostKeys
- User
- UserKnownHostsFile
- VerifyHostKeyDNS
-Pport-p is already reserved for preserving the times and modes of the file.-p-q-rMan Openssh Sftp-server
scp follows symbolic links encountered in the tree traversal.-Sprogram-Tscp checks that the received filenames match those requested on the command-line to prevent the remote end from sending unexpected or unwanted files. Because of differences in how various operating systems and shells interpret filename wildcards, these checks may cause wanted files to be rejected. This option disables these checks at the expense of fully trusting that the server will not send unexpected filenames.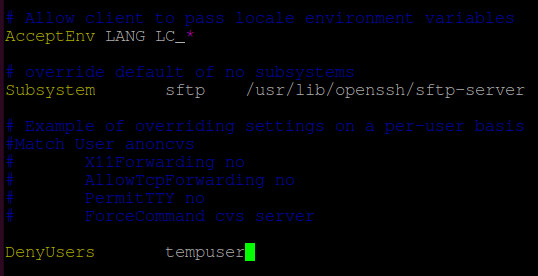
-vscp and ssh(1) to print debugging messages about their progress. This is helpful in debugging connection, authentication, and configuration problems.The scp utility exits 0 on success, and >0 if an error occurs.
sftp(1), ssh(1), ssh-add(1), ssh-agent(1), ssh-keygen(1), ssh_config(5), sshd(8)
scp is based on the rcp program in BSD source code from the Regents of the University of California.
Timo Rinne <tri@iki.fi>
Tatu Ylonen <ylo@cs.hut.fi>
From the SSH man page:
ssh (SSH client) is a program for logging into a remote machine and for executing commands on a remote machine. It is intended to provide secure encrypted communications between two untrusted hosts over an insecure network. X11 connections, arbitrary TCP ports and UNIX-domain sockets can also be forwarded over the secure channel.
The information provided on this page only covers a small portion of the things you can do with SSH and it is recommended that you read more about it via the man page or from other sources.
Required Client Software
Linux/Unix/macOS
OpenSSH is typically packaged with most Unix and Linux variants, which includes macOS. You can verify that ssh is installed by opening a terminal and running the following command:
Windows
Since April of 2018, SSH (OpenSSH) comes pre-installed in Microsoft Windows 10 and above and can be used via the command line either by using the CMD shell or Powershell. More information can be found at Microsoft's OpenSSH in Windows page.
You also have the option to run a 3rd party product called PuTTY. However, PuTTY uses different configurations for SSH Keys, X-Forwarding, etc. so, you'll need to find documentation for those items online. The information you see below is specifically for OpenSSH, not PuTTY.
Using SSH
Connecting to a Remote System
For most of your connection needs in the CS Department, once you have confirmed that an SSH client is installed on your system, you can create a basic connection to a remote CS Linux client using the following syntax:
Note: When typing your password, nothing will appear in the terminal. If you think you mistyped your password, you can press Ctrl+U to clear the input and try again.
For example, to connect to one of our Ugrad Linux clients, say, ugrad5, and your username on that system is ckent1, simply use:
Man Opens Sharks Mouth
Using an Alternate Port
The default connection port for SSH is TCP port 22, but sometimes you'll need to use an alternate port for any number of reasons. To do this, you can use the -p parameter. For example, if you need to connect on TCP port 2096:
Connecting with Key-Based Authentication
A very common authentication method built into SSH is key-based authentication. Instead of using a password to authenticate, a server may pre-authenticate a client by installing a public key. This system is far more secure than basic password authentication and is available on all CS Linux clients.
For more information, please see our Accessing Linux Clients with SSH Public Key Authentication page.
X11 Forwarding
SSH isn't just for running remote terminal sessions. It can also be used to run GUI applications remotely. You can do this using a system called X11 Forwarding.
Required Client Software for X11 Forwarding
Linux
If you're running a GUI on Linux, you probably already have X installed. You can verify with the following command:
Windows
For X forwarding to work properly on Microsoft Windows, you will need to install an X window server, for example, a program like VcXsrv.
macOS
Even though macOS is technically running a variation of X, you won't be able to use it for standard X applications like SSH. In order to accomplish this, you can install XQuartz.
Using X11 Forwarding
In order to enable X11 forwarding in your SSH connection, you will need to use the -X parameter:
Once the session is established, you should be able to invoke any GUI application simply by executing the command.
Port Forwarding
SSH has the ability to forward TCP traffic over the connection to enable the client to connect to resources on the remote system or vice versa.
Local Port Forwarding
If you want to connect to a service that is only accessible via the server you're connecting to, but want to be able to access it on your local PC, you can accomplish this using a local port forward using the -L parameter.
Let's assume the server you're connecting to has access to a MySQL server that only accepts connections on port 3389 from your server, but you want to be able to use the management tool on your laptop to be able to make a change to the database. You can run the following command:
This will open a local socket on TCP port 3390 and forward all traffic to remote socket on the SSH server. If you point your mysql tool to port 3390 on 127.0.0.1, the SSH server will attempt to connect to mysql.remote.host on TCP port 3389 and forward all traffic back through the tunnel to your client.
Remote Port Forwarding
Man Openssh
If you have a local service that you want the server to be able to access, you can accomplish this using the -R parameter to invoke a remote port forward.
Let's say you're trying to download the latest version of nmap on your server, but the domain is blocked by the network security team. You can allow the server to connect through your own connection instead by using the following command:
On the server, you can now connect to port 8080 on 127.0.0.1, which will allow you download your software.
Dynamic Port Forwarding
Man Openssh-server
In the event that there are a bunch of resources you need that are only available on the server's network, you can create a dynamic port forward using the -D flag:
This will create a SOCKS5 proxy on the local port specified to be able to filter traffic through the server. This is a great way to create a very simple VPN.
Configuring SSH
There are a lot of parameters you can set for your SSH connections, and remembering them can be a chore. Fortunately there is an easy way to do this with SSH's client configuration file.
Setup
Typically the file can be found at ~/.ssh/config. If you'd like to save it in another location or have different config files, you can specify which to use with the -F flag:
If the file does not already exist, you can safely create it. Just make sure to set the appropriate permissions on the file. The .ssh directory should be be set to Read, Write, and Enter for the owner only, and any config files should be set to Read and Write for the owner only:
Configuration
The SSH config file has a relatively straightforward syntax:
Each Host line is followed by the settings for that host. You can specify settings for multiple hosts with a new Host line. For example:
When you connect to a host, SSH will scan the config file to determine if there is a matching Host entry for the server you're attempting to connect to. This allows us to use a wildcard character (*) in this field for pattern matching. For example:
Note: If multiple patterns match a host, the settings will stack. In this case, any host matching Host *.jhu.edu also matches Host *, so the settings from both will apply. If the same parameter is set in different matching Host sections, the first one in the file will be the one that takes effect.
You can find a list of all parameters available in the ssh(5) Man Page.
Useful Examples
Preventing Disconnects on JHU Servers
The primary firewall maintained by JHU IT gets millions of connections going through it at time, so reducing the number of stale connections is important to prevent the networks from becoming overloaded. Unfortunately, this can cause some issues with SSH connections if they don't see enough activity. We can prevent this from happening by using the ServerAliveInterval and ServerAliveCountMax parameters.
From the ssh(5) Man Page:
- ServerAliveCountMax
- Sets the number of server alive messages (see below) which may be sent without ssh(1) receiving any messages back from the server. If this threshold is reached while server alive messages are being sent, ssh will disconnect from the server, terminating the session. It is important to note that the use of server alive messages is very different from TCPKeepAlive (below). The server alive messages are sent through the encrypted channel and therefore will not be spoofable. The TCP keepalive option enabled by TCPKeepAlive is spoofable. The server alive mechanism is valuable when the client or server depend on knowing when a connection has become inactive.
- The default value is 3. If, for example, ServerAliveInterval (see below) is set to 15 and ServerAliveCountMax is left at the default, if the server becomes unresponsive, ssh will disconnect after approximately 45 seconds. This option applies to protocol version 2 only.
- ServerAliveInterval
- Sets a timeout interval in seconds after which if no data has been received from the server, ssh(1) will send a message through the encrypted channel to request a response from the server. The default is 0, indicating that these messages will not be sent to the server. This option applies to protocol version 2 only.
What we're going to do is enable a ServerAliveInterval that sends every 30 seconds and increase the ServerAliveCountMax from 3 to 5 just for a little extra buffer.
Giving a Connection a Nickname

Lets say you have a number of connections that have some really hard to remember hostnames or that need different kinds of parameters on the same server. Since the config file is a pattern match of the command line parameter, we can hijack it to specify which server we actually want to connect to by using HostName.
From the ssh(5) Man Page:
- HostName
- Specifies the real host name to log into. This can be used to specify nicknames or abbreviations for hosts. The default is the name given on the command line. Numeric IP addresses are also permitted (both on the command line and in HostName specifications).
Openssh Man Ssh-keygen
Assume we have the following config file:
Now instead of typing this:
Openssh Client Windows 10
We can type this and it will do the same thing:
Additional Resources
